Note: When configuring the LDAP server, the query string format on the server should contain the name of the group configured on SX II.
You can use the Lightweight Directory Access Protocol (LDAP) to authenticate SX II users instead of local authentication.
Lightweight Directory Access Protocol (LDAP/LDAPS) is a networking protocol for querying and modifying directory services running over TCP/IP.
A client starts an LDAP session by connecting to an LDAP/LDAPS server (the default TCP port is 389). The client then sends operation requests to the server, and the server sends responses in turn.
Reminder: Microsoft Active Directory functions natively as an LDAP/LDAPS authentication server.
The LDAP section expands. If it does not, click on the LDAP section header.
Server Configuration
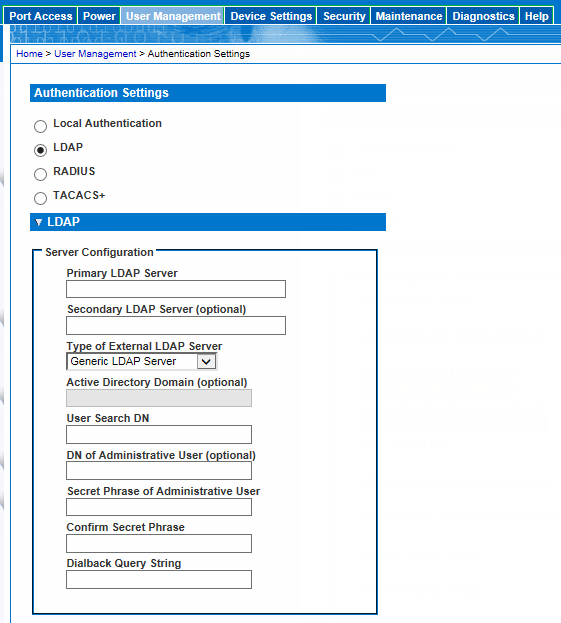
Complete this field if your LDAP server only allows administrators to search user information using the Administrative User role.
Consult your authentication server administrator for the appropriate values to type into this field.
An example DN of Administrative User value might be: cn=Administrator,cn=Users,dc=testradius,dc=com. Optional
Enter the password in the Secret Phrase field and again in the Confirm Secret Phrase field.
LDAP/LDAP Secure
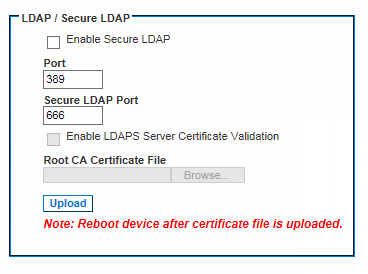
This will enable the Enable LDAPS Server Certificate Validation checkbox.
Secure Sockets Layer (SSL) is a cryptographic protocol that allows SX II to communicate securely with the LDAP/LDAPS server.
When the "Enable Secure LDAP" option is selected and the "Enable LDAPS Server Certificate Validation" option is selected, the DNS name must be used to match the CN of LDAP server certificate.
If you do not want to use the previously uploaded root CA certificate file, leave this checkbox deselected.
Disabling this function is the equivalent of accepting a certificate that has been signed by an unknown certifying authority. This checkbox is only available when the Enable Secure LDAP checkbox has been enabled.
Note: When the Enable LDAPS Server Certificate Validation option is selected, in addition to using the Root CA certificate for validation, the server hostname must match the common name provided in the server certificate.
This field is enabled when the Enable Secure LDAP option is selected.
Consult your authentication server administrator to get the CA certificate file in Base64 encoded X-509 format for the LDAP/LDAPS server.
Use Browse to navigate to the certificate file.
If you are replacing a certificate for the LDAP/LDAPS server with a new certificate, you must reboot the SX II in order for the new certificate to take effect.
Test LDAP Server Access
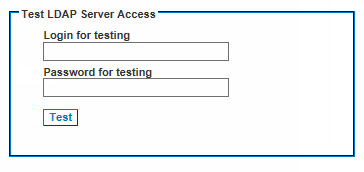
This is the username and password you entered to access the SX II. It is also username and password the LDAP server uses to authenticate you.
The SX II then tests the LDAP configuration from the Authentication Settings page. This is helpful due to the complexity sometimes encountered when configuring the LDAP server and SX II for remote authentication.
Once the test is completed, a message is displayed that lets you know the test was successful or, if the test failed, a detailed error message is displayed. It also can display group information retrieved from remote LDAP server for the test user in case of success.